Cybersecurity: Risk assessment
For companies to survive and thrive, they need to be skilful in understanding and managing their existential risks. Some of these existential risks include technology disruption, global economic downturn, supply chain disruption, regulatory changes and cybersecurity risk. Cybersecurity risk is emerging as one of the fatal risks companies face today as they continually develop and maintain their digital ecosystem. The criticality of the digital ecosystem of most companies cannot be overstated. It extends to external customer channels (including mobile, web and social), internal enterprise resource planning systems, partner systems and critical national infrastructure (e.g. financial services). Cybersecurity risk management underpins identifying, assessing and estimating potential compromise to essential elements of the digital ecosystem, including business information systems, data (customer and business) and services (i.e. internal and external). Cybersecurity risk management has become a significant cornerstone that enables the digital ecosystem’s confidentiality, integrity and availability. As such, companies require a balanced approach to manage cybersecurity risk.
Extreme and non-risk-based measures can incur high costs, leading to business bankruptcy. At the same time, lackadaisical actions can lead to unacceptable breaches that can undermine the company. The balanced approach must utilise suitable risk-based practices, including risk assessment and threat modelling. Both are highly recommended practices by companies to understand their risk exposures and manage their risk position. They enable senior management to align with the board-set risk appetite.
What is risk assessment?
Risk assessment is an essential stage in risk management. It underpins and enables other risk management stages, including prioritising relevant risk, determining a company’s risk appetite and defining initiatives to minimise risk. It fundamentally helps the company to answer the question, “What is at stake?“. Examples of “what is at stake” from recent cybersecurity breaches include significant material fines, reduction in company share prices, loss of earnings, legal actions, prison time for executives, and regulatory penalties.
| Example of “what is at stake” in a telecommunications cyber attack The attack on a telecommunications company entailed using a two-pronged approach. The first was a Distributed Denial of Service (DDoS) attack, while the second was a SQL Injection attack. Some commentators opine that the DDoS attack (i.e. overloading digital systems) was a diversionary tactic so that the SQL Injection attack could sail under the radar undetected. The SQL injection attack was made possible by exploiting an outdated version of MySQL with known software bugs. This exploit resulted in the exfiltration of 157,000 customer personal data, including name, address, date of birth, email address and financial information. The database was hacked via an insecure legacy web page acquired during a company merger. This cybersecurity attack cost the telecommunications company around £60m and led to a loss of over 100,000 customers. Other costs included fines and brand damage from the Information Commissioner’s Office (ICO). |
Companies follow a series of qualitative and quantitative risk assessment methodologies to understand “what is at stake“. The NIST SP-800-30, ISO/IEC 2005:2018 and the ISF frameworks are the most common risk assessment methodologies most companies use. They provide a robust framework for companies to identify, assess and manage their risk posture. Each of these methodologies has its unique approach to risk assessment, and they still share some similarities. A review of the NIST SP-800-30 risk assessment methodology includes five steps in the assessment phase. The five steps in the assessment phase include
- identifying threat sources and events,
- identifying vulnerabilities and predisposing conditions,
- determining the likelihood of occurrence,
- the magnitude of impact, and
- the risk.
Identifying threat sources and events allows the company to answer “who wants to attack me” and “how can they attack me”. Providing this intelligence to the company is topmost on the priority list of most Chief Information Security Officers (CISO) or Cybersecurity Directors. The national cybersecurity strategy lends itself to this question by identifying the threat actors, including cybercriminals, terrorists, states/sponsored states, hacktivists and script kiddies.
| Example of “Who wants to attack the company?” and “How can they attack the company?” The attack on an American entertainment company entailed using malware. The malware identified was WannaCry. The company was breached three times with different WannaCry versions. The malware’s delivery mechanism was through spear-phishing emails. Hackers identified the recipients (i.e. staff) of the spear-phishing emails using social media sites, including Facebook. The spear-phishing email included malware attachments.Further Federal Bureau of Investigation (FBI) analysis showed that the malware included 10,000 hard-coded hostnames. This knowledge implied extensive research from living inside the company’s network for several months undetected. The first attack happened before the release of a movie which cost 44 million dollars, which appeared to be the motivation for the attack. The hackers demanded that the company cancel the planned release of a movie. The timeline of the hack coincided with a letter sent by a government to the United Nations to censor the movie release as if not done, and it would amount to another government sponsoring terrorism. Based on this and other evidence, the threat actor appears to be either a state or a state surrogate. |
The second step of the assessment phase is identifying vulnerabilities. To most companies, identifying vulnerabilities answers the question, “What’s our exposure?”. A company’s exposure is the perimeter of its exploitable attack surface. Usually, this includes human, application, or network attack surfaces. Most large companies utilise external consultancy to understand their exposure due to their size, need for in-depth specialist knowledge and the need for a neutral, independent view. This approach, although expensive, is more thorough and easily stands up to scrutiny. The exposure report or top risks leverages proprietary external security consultancy frameworks or other industry best practices. Specific company knowledge is elicited using staff interviews, questionnaires, specialist domain reviews, empirical data collection, and technology testing tools to implement the adopted frameworks. Generally speaking, reducing cybersecurity exposure is a challenge for organisations. The ways and activities companies seek to deliver better value to their customers by improving performance and profitability are the things that increase their cybersecurity risk exposure. Also, every pound spent on cybersecurity is a pound not spent on other business activities.
| Example of “What’s the company’s exposure?” for a financial services company A financial service company was attacked some years ago by exploiting the vulnerability in its information technology systems (i.e. application, network and infrastructure). The vulnerability identified was in an outdated Apache struts publicly accessible online. The specific version of Apache struts used by the company was vulnerable and required patching. Apache Struts is a web application framework for creating Java Enterprise Edition web applications. It enables the model, view and controller architecture of applications that support the company’s digital ecosystem, including web, mobile and social interactions for customers. Hackers exploiting this vulnerability resulted in this financial service company paying up to 700 million dollars in settlement to the US for the data breach of nearly 150 million people. |
The other steps of the risk assessment phase are determining the likelihood, assessing the magnitude and identifying the risk scale. Companies compute the likelihood of threat events causing adverse impacts by calculating both the likelihood of a threat occurring and the likelihood of its successful exploitation. For both a technique that factors in the type of adversaries (including cybercriminals, terrorists, states/sponsored states, hacktivists and script kiddies), their skill level, history of similar attacks and the effort required is factored in.
For companies, assessing the magnitude entails understanding the impact on business processes and services. These business processes and services include the channels used to relate with customers, deliver value, collaborate with partners and suppliers, and generate income. Also, the impact on business assets, customers/staff, other organisations (including partners and suppliers) and the nation at large must also be understood and computed accordingly.
| Example of “Cyberattack impact?” for a financial services company Arguably, one of the most significant data breaches on a financial services company occurred in 2017. The data breach affected over 147 million people in the United States, Canada and the United Kingdom. The cybercriminals stole their personal data, including Social Security numbers, dates of birth, and addresses. The financial cost on the financial services was over 600 million dollars, including costs associated with investigating the breach, providing credit monitoring services to affected customers, regulatory financial penalty and reduced valuation due to the company stock price drop. The non-financial costs on the financial services company include damage to reputation/brand and increased regulatory scrutiny. Also, to its customers, the impact includes an increased risk of identity theft, financial costs due to successful cyber attacks and emotional distress. |
Using the value of both likelihood and magnitude allows the company to understand the scale of their risk. The risk is identified by interpreting these critical indicators on this calibrated risk assessment matrix.
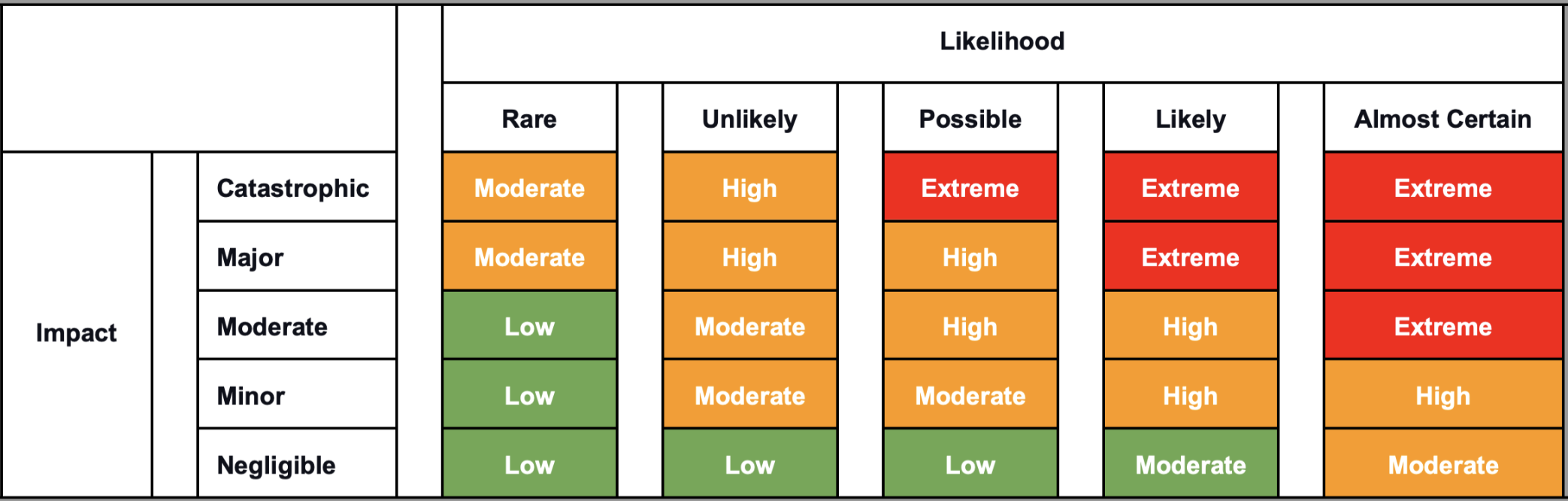
Table 1: Risk assessment matrix
In turn, the output of their risk assessment drives their risk response activities until they operate within their board-set risk appetite.
In conclusion, cyber risk assessment is now a must for thriving companies because it helps them make informed decisions, improve cybersecurity resilience, reduce costs, enhance their reputation, increase agility and, most importantly, mitigate their existential cybersecurity risk.

